|
A Test Instrument for HF/LF RFID |
||||||||||||||||||||
|
This device can do almost anything involving almost any kind of low-(~125 kHz) or high-(~13.56 MHz) frequency RFID tag. It can act as a reader. It can eavesdrop on a transaction between another reader and a tag. It can analyze the signal received over the air more closely, for example to perform an attack in which we derive information from the tag's instantaneous power consumption. It can pretend to be a tag itself. It is also capable of some less obviously useful operations that might come in handy for development work.
This flexibility is achieved using digital signal processing techniques. The signal from the antenna is either immediately followed by an A/D, or digitized after only a little bit of analog processing to improve the signal's dynamic range. The subcarrier frequencies for many of the high-frequency tags (e.g. the ISO-standard tags) are fast; it would be possible to filter for them in software, but impractical with a general-purpose CPU. I therefore route the signal from the A/D through a small FPGA; this can either relay the signal to the micro, over a synchronous serial port, or perform the filtering operations itself, in hardware, and pass only the result to the micro. The latter option greatly reduces the workload of the micro.
Since the signal processing is performed almost entirely in software (or in the FPGA), it is possible to reconfigure the device for a completely different modulation scheme with only software changes. This flexibility is also useful when looking for other information in the signal sent over the air; for example, it would be helpful when trying to perform a power attack. The proxmark3 is an improved version of my proxmarkii. The proxmarkii had a slow A/D, and no FPGA assist for the signal processing; this made it impractical to deal with many of the ISO-standard (and other) 13.56 MHz tags, which now represent a large fraction of the market. The proxmarkii was also incapable of bypassing the peak-detector hardware and going straight from the antenna to the A/D, a mode that might be useful for certain eavesdropping operations. Finally, the proxmarkii lacked some minor but useful features, such as the ability to derive its timing from the incident carrier (as opposed to its own crystal) while pretending to be a 13.56 MHz tag. I consider the proxmarkii to be obsolete, and inferior in every way to this latest device.
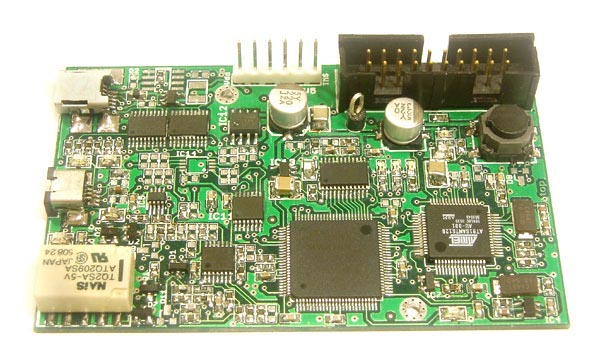
The hardware is built on a four-layer printed circuit, laid out to 8/8 thou rules with an 0.4 mm minimum drill size. The entire unit is about the size of a playing card. The largest IC is the FPGA; the ARM7 is to its right. The tall component at the bottom left is a relay, which is an easy way to cope with the large dynamic range of the signal from the antenna in `read' (we drive the antenna ourselves, hard) vs. `eavesdrop' (we see only the signal received over the air) modes. Most of the passives and small ICs on the left side of the device are part of the analog signal chain. The very large header is for JTAG to the ARM, with the standard pinout. The six-pin single-row header is for JTAG to the FPGA, again with the standard pinout. (These are needed only for debugging; the ARM executes code out of flash, and can reprogram itself over USB, and the FPGA is configured by the ARM.) The USB connector is clearly visible at the top left, and the antenna connector is below it. An effort is made at USB compliance, but not a very strong one. I think that the hardware should be capable of that, if anyone cares. The only thing that might be doubtful is the power consumption in suspend, and there is a big FET switch that can turn everything except the ARM off. In practice, it all just works. The software is at this point minimal. All systems software is provided; this includes the bootloader, the FPGA loader, and a debug logger that works over USB. I've written software to support a few different kinds of tag; for example, I can:
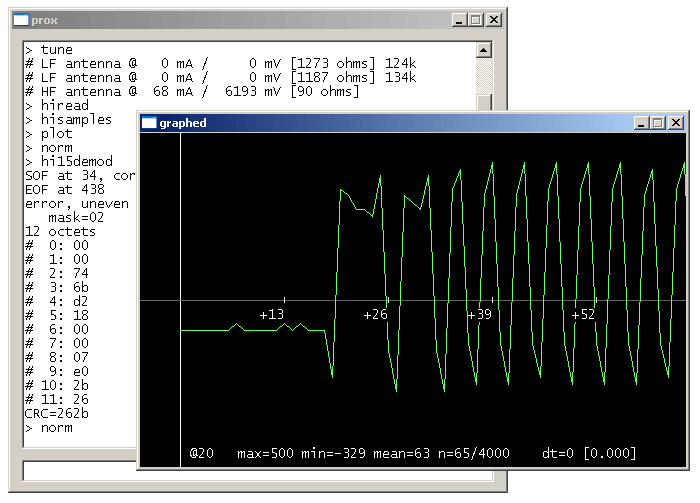
The trace below is the beginning of the `Inventory Response' transmitted by a TI Tag-It Plus (ISO15693) transponder, in response to the `Inventory Request' command that I sent:
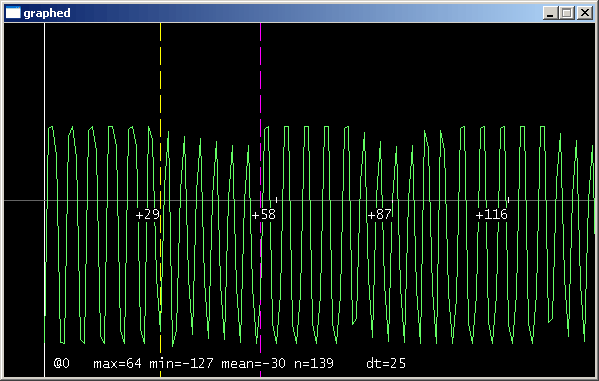
Low-frequency tags are supported in exactly the same way as for my previous designs: a fast A/D acquires one sample per carrier cycle, and further processing occurs in software. For example, here is a trace from an HID Prox Card II:
This trace might be demodulated, to obtain the card's ID, or we might just replay it verbatim, to clone the card. Most of the software is written in C, for arm-elf-gcc. For the numerical stuff it looks like I could get maybe a factor of two speedup by hand-coding in assembly, but I haven't. I can eavesdrop on ISO 14443 in real time, so there's no reason to make it faster. A release is available for download:
There is an omission in the bill of materials; RLY1 should be Digikey 255-1010-5-ND. The software and other materials in proxmark3-may23-2007.zip may be distributed and modified according to the terms of the GPL; see the license in the zip file. The printed circuit board data are available separately:
A number of people have built units from these plans. Among them are a group in Nijmegen that reports several attacks against Mifare Classic, and demonstrates them using a proxmark3. Additional information is available from proxmark.org or Edouard Lafargue's manual, though I have no affiliation with either site. I don't have any plans for new development of this project. It's semi-actively developed by others, with an SVN repository on Google Code. Feb 2009, near Seattle |